As ransomware and cyber threats evolve in complexity, the role of backup platforms like Veeam has shifted from a reactive recovery tool to a critical component of proactive cyber defense. This article explores how integrating Veeam Backup & Replication with Security Information and Event Management (SIEM) platforms significantly enhances organizational security posture, supports compliance, and accelerates incident response.
1. The Need for SIEM Integration
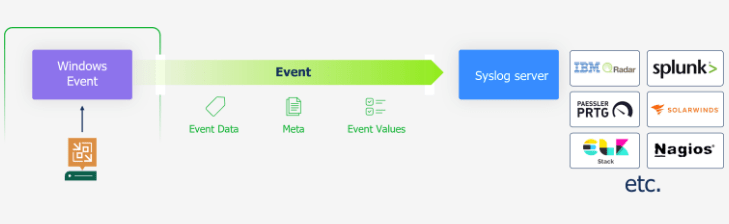
Modern cybersecurity strategies rely on centralized visibility. SIEM platforms aggregate, analyse, and correlate logs from various sources, including firewalls, endpoint protection, identity providers, and increasingly, backup systems. As attackers frequently target backups to sabotage recovery efforts, ensuring backup visibility within a SIEM is no longer optional—it’s essential.
2. Why Veeam Backups Matter in Your SIEM Strategy
- High-Value Targets: Backups are often the last line of defense in a ransomware attack. When targeted and compromised, recovery becomes nearly impossible.
- Behavioural Insight: Veeam logs can reveal suspicious patterns, such as failed jobs, sudden deletions, off-hours activity, or unauthorized configuration changes.
- Proactive Detection: By feeding these events into a SIEM, security teams can detect threats in real time and initiate response workflows. Early detection of anomalies can be a vital defense against potential malicious activities, ensuring the security of your data and services.
3. Key Benefits of Integration
Enhanced Visibility Backup logs are treated as first-class telemetry. SIEMs can correlate Veeam events with data from EDR, IAM, and firewall systems for holistic threat detection.
Accelerated Incident Response Integrated logs enable real-time alerting and response automation via SOAR capabilities. For example, a backup job deletion alert can trigger investigation workflows or isolate systems.
Compliance and Auditing Regulatory standards such as ISO 27001, GDPR, and NIST require proof of secure data handling. SIEM integration provides centralized, immutable audit trails of backup operations.
Reduced Alert Fatigue Instead of generating siloed alerts, backup events are contextually analysed with broader security data, reducing false positives and prioritizing real threats.
4. How It Works: Integration in Action
- Log Collection: Veeam emits logs of job statuses, errors, credential changes, and other operational events.
- Log Forwarding: These logs are forwarded via syslog or API to SIEM platforms like Splunk, Microsoft Sentinel, or QRadar. Map Veeam events to common information models (CIM) for normalization
- API-Based Integration: User Veeam Enterprise Manager REST API to extract backup metadata and create customer connectors for SIEM platforms to ingest the backup health data. Monitor for critical events like failed backups, suspicious delete operations
- Event Correlation: The SIEM correlates backup events with data from the wider infrastructure to detect anomalies such as unusual backup size changes with network traffic spikes and backup file modifications with known malware indicators.
- Automated Response: SIEM or SOAR tools can respond by raising tickets, notifying SOC teams, or isolating affected assets.
5. Use Cases
- Ransomware Detection: Correlate backup encryption attempts with endpoint security alerts
- Insider Threat Monitoring: Detect unauthorized access to backup consoles or data
- Compliance Auditing: Prove backup completeness and integrity for regulatory requirements
6. From Backup to Cyber Control Point
Integrating Veeam with your SIEM transforms your backup infrastructure into an active security layer. This approach ensures not only recoverability but also real-time threat visibility and automated defense. As ransomware tactics grow more sophisticated, this integration is a critical step toward building a resilient, compliant, and secure enterprise.
Published: July 15, 2025 12:13pm
Leave a comment